Home

Our company
We understand the complexities of our clients’ business model and deliver solutions that fit their needs
15Years in Business.
Learn more about our Success Stories
XentIT is an Information Technology firm specializing in Cybersecurity & Compliance, Managed Cybersecurity, Cloud Technologies, DevOps, and Information Technology Resale Services. We Function as a virtual and seamless extension of our client’s service and delivery organization providing high-value, high-performance, and high-quality business information solutions.
Our Services
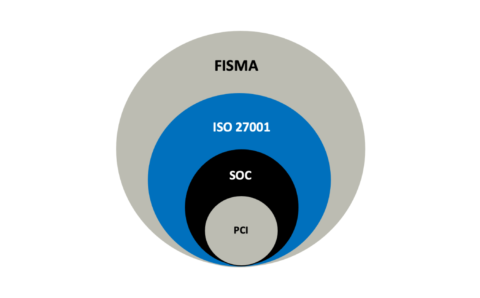
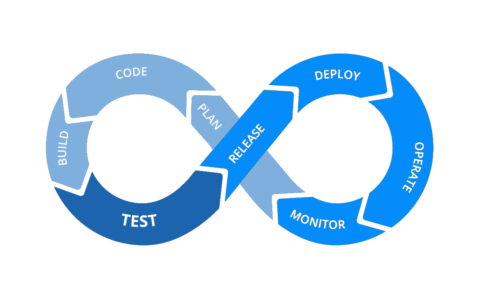
XentIT Managed Cybersecurity Services.
1000
+
Clients
3
M+
Endpoints Protected/Managed
45
+
United States & Tribal Nations Served
50
+
Clients in Canada & Caribbean Nations
Case studies
Proud projects make us excel
Blogs & news
Interesting articles
XentIT appoints Khalid Alvi as Executive Vice President
Landover, MD – January 16, 2023 – XentIT, a cybersecurity, cloud and managed services company, and NIT, its wholly owned subsidiary, with offices in Landover, …
XentIT is part of Graham Technologies team that has been awarded a 10 year $2.1B NOAA NMITS BPA. We look forward to work with William Graham and his team in supporting NOAA’s mission and program objectives.
Graham Tech won a NOAA Mission Information Technology Services contract to provide adaptive, timely solutions for NOAA organizations to satisfy current and …
Some of Our Elite Clients.
Accentuate IT, Achieve Results.

Department of Justice, US

National Institutes of Health, US

NASA, US

Securities and Exchange Commission, US

Department of Homeland Security, US

Prisma Health, US

Navicent Health, US

American Automobile Association, US

Rolex Watch, US

General Dynamics IT, US

Peraton, US